Defend Your Cookies with Essential Web Security Tactics
Evergreen
🌳Last tended Feb 08, 2020
Web Development
Illustrated Notes
Between IoT botnet attacks, Bitcoin ransomware, and the weekly cadence of high-profile data breaches, doing anything on the internet feels like playing Russian Roulette.
And that's just for normal people using it.
If you're a developer, you're partially responsible for protecting all those normal people from the horrors of whatever
Thankfully, you do not have to brave the black hat darkness alone.
I am (thankfully) not responsible enough for anyone to put me in charge of security for an important website. But I was still curious.
I wanted to know what the current landscape of internet risk looks like. How, exactly, is LulzSec going to hack into my mainframe in 2020?
Here's my illustrated notes from Mike's course that should give you a big picture overview of what to should look out for.

Turns out there's a small set of fairly well-known and easy to defend attacks that we can protect ourselves from:
- Man in the Middle (MITM)
- Cross-Site Request Forgery (CSRF)
- Cross-Site Scripting (XSS)
Shielding yourself from these three is a great starting point. It's at least enough to keep the


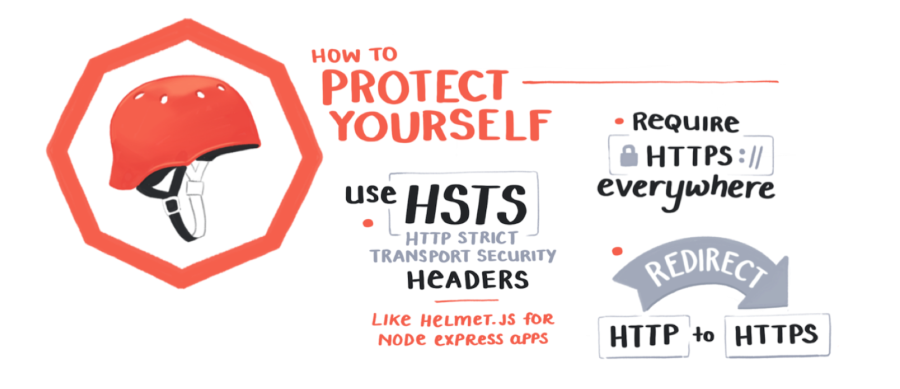
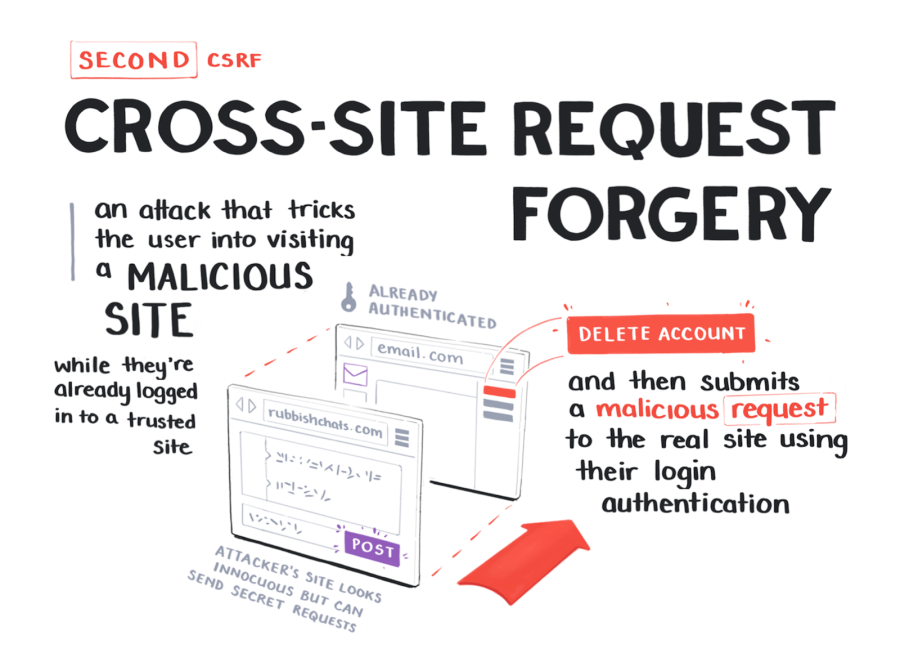

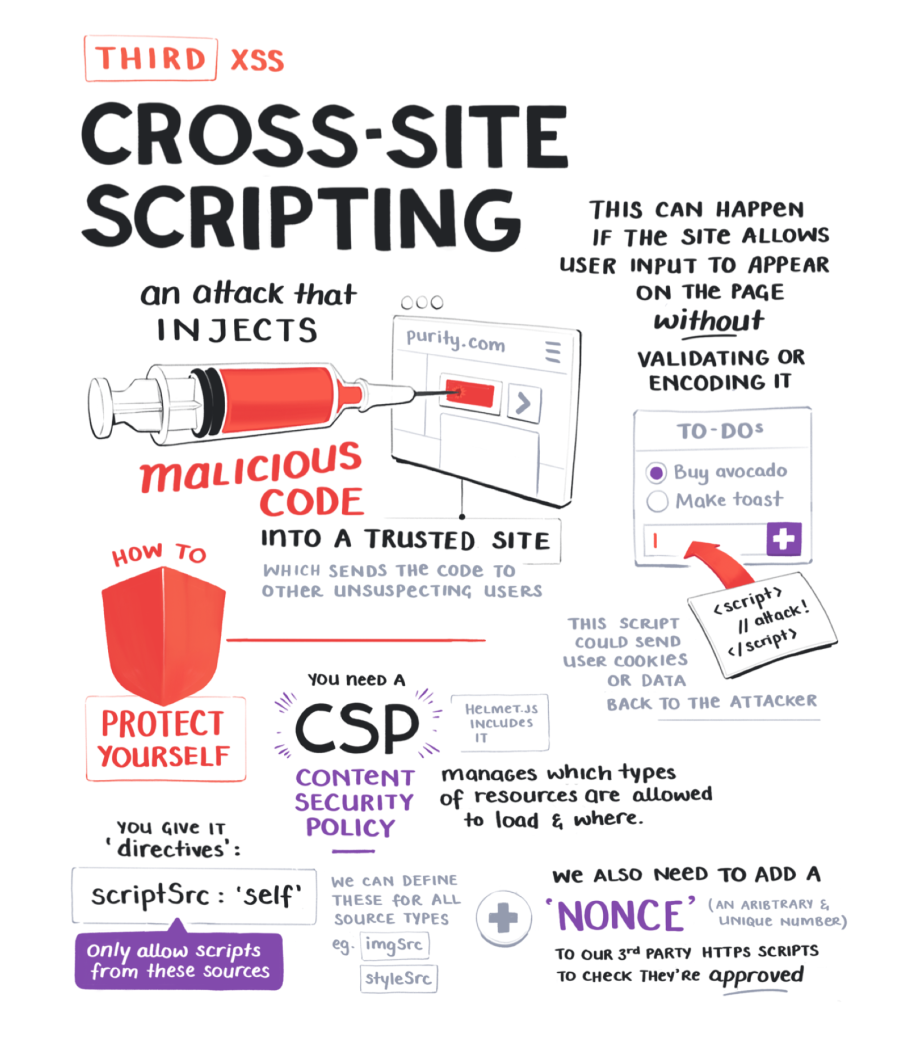
Keeping out this trio of attacks will go a long way.
If (unlike me) you are responsible enough to be in charge of security for a moderately-sized website, it might be worth double checking you have these protections in place.
Better safe than sorry. Especially when sorry means you end up on the front page of Hacker News in this week's edition of obviously preventable security breaches.
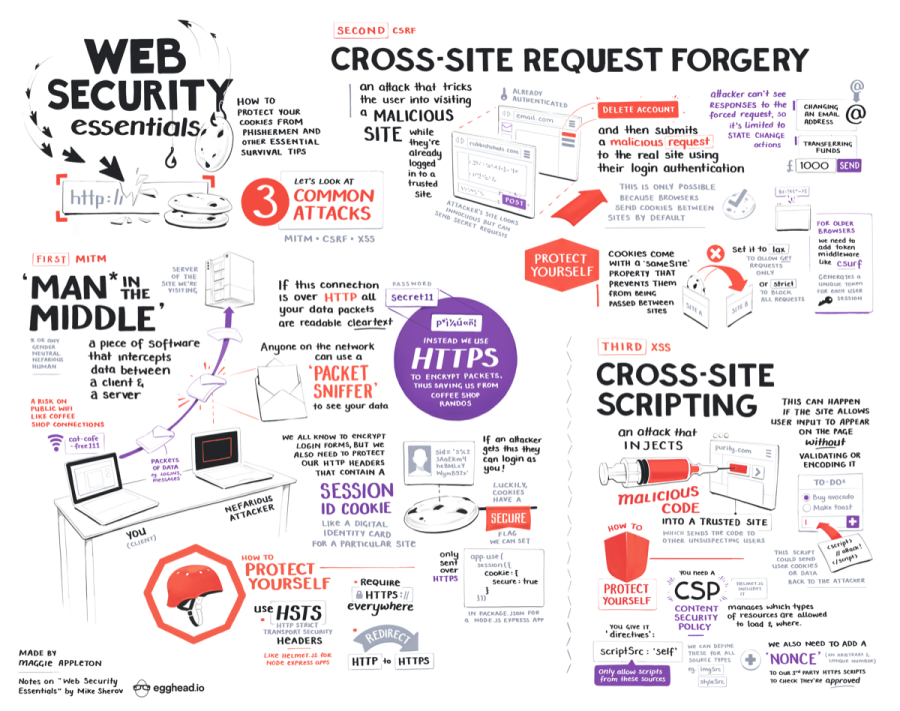
Want more illustrated notes on web development?
Take a look at
Linked References
The Art and Craft of Gatsby Themes
More illustrated notes, this time on Gatsby themes . They're one of the newer features in Gatsby.js – little building blocks of site functionality you can mix n' match n' share on NPM. Chris…
Speaking the GraphQL Query Language
GraphQL is undoubtedly one of the popular kids on the Web Development playground right now. If you haven't heard of GraphQL, the TLDR is that it's a new way to request data from an API. If you're…
Instachatting with Vue & Socket.io
The intantness of chat apps has always been a mystery to me. The technical details of moving emojis through The Internet Pipes and across continents in 0.004 miliseconds is well beyond my paygrade…